
Pic 1-Shutterstock
Introduction:
In today’s interconnected world, the security of operational technology (OT) systems is of paramount importance. However, the traditional approach of relying solely on an OT Security Operations Center (SOC) has proven to be inadequate. This blog post explores the failure of OT SOC and the emergence of the Zero Trust Policy as a more effecve solution. We will delve into the challenges faced by OT SOC, the limitations of its approach, and how the Zero Trust Policy offers a more robust and proactive security framework.
Failure of OT SOC:

Pic 2- Solutions Review
OT SOC, which focuses on monitoring and protecting OT systems, has faced numerous challenges that have contributed to its failure. One of the primary issues is the lack of visibility into OT networks. Traditional SOC tools are designed for IT networks and struggle to provide comprehensive visibility into OT systems. This blind spot leaves OT networks vulnerable to atacks that go undetected, leading to potential disruptions and compromises.
Another challenge is the reliance on signature-based detection methods. OT SOC often relies on known attack signatures to identify threats. However, this approach is ineffective against zero-day attacks and sophisticated threats that employ advanced evasion techniques. As a result, OT SOC fails to detect and respond to emerging threats on time, leaving critical infrastructure exposed.
Furthermore, the reactive nature of OT SOC exacerbates its failure. Traditional SOC models are primarily focused on incident response rather than proactive threat hunting. This reactive approach leaves OT systems vulnerable to attacks that can cause significant damage before they are detected and mitigated.
The Limitations of OT SOC:
The limitations of OT SOC extend beyond its technical challenges. One of the key shortcomings is the lack of integration between IT and OT security teams. OT SOC often operates in isolation, disconnected from the broader security ecosystem. This siloed approach hampers effective collaboration and information sharing, impeding the ability to detect and respond to threats holistically.
Pic 3 – TechTarget
Additionally, OT SOC struggles to keep pace with the evolving threat landscape. As cyber threats become more sophisticated and targeted, OT SOC must continuously adapt its defenses. However, the lack of dedicated resources and expertise in OT security often hinders the ability to implement and maintain robust security measures.
The Rise of Zero Trust Policy:
In response to the failure of OT SOC, organizations are turning to the Zero Trust Policy as a more effective security framework. The Zero Trust Policy operates on the principle of “never trust, always verify.” It assumes that no user or device should be inherently trusted, regardless of their location or network.
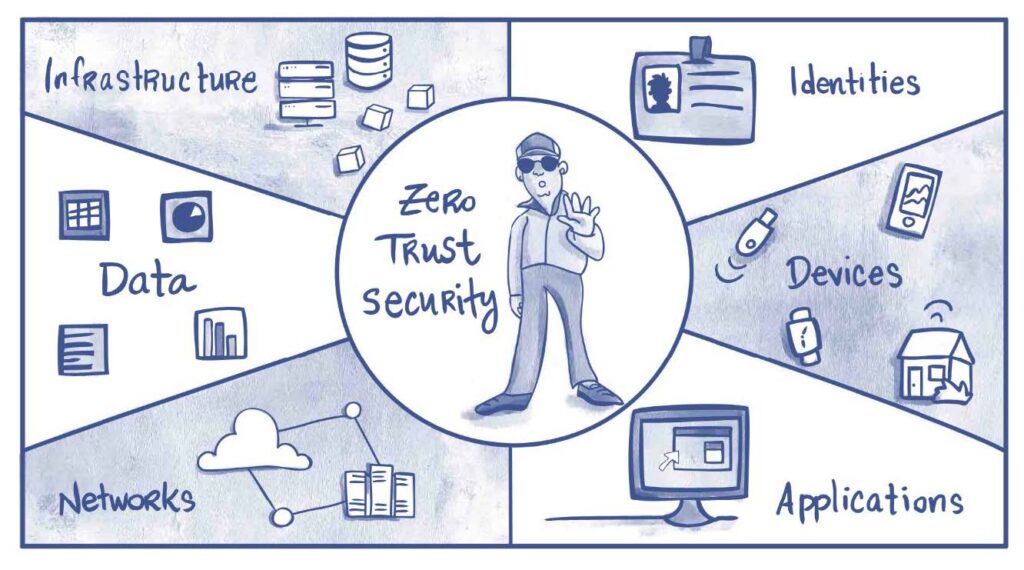
Pic 4 – Strong DM
Unlike OT SOC, which relies on perimeter-based security, the Zero Trust Policy adopts a holistic approach that focuses on securing individual assets and data. It incorporates multi-factor authentication, micro-segmentation, and continuous monitoring to ensure that only authorized users and devices can access critical resources.
Furthermore, the Zero Trust Policy emphasizes the importance of granular access controls. It enforces the principle of least privilege, granting users only the necessary access rights to perform their tasks. This minimizes the attack surface and reduces the potential impact of a security breach.
Conclusion:
The failure of OT SOC highlights the need for a more proactive and comprehensive security approach. The Zero Trust Policy offers a promising alternative by addressing the limitations of OT SOC and providing a robust framework for securing OT systems. By adopting the Zero Trust Policy, organizations can enhance their security posture, mitigate risks, and ensure the uninterrupted operation of critical infrastructure. As the threat landscape continues to evolve, embracing innovative security strategies like the Zero Trust Policy becomes imperative to safeguarding our interconnected world.
Author: Sanjeev Sharma
Pictures Courtsey:
Pic 1-Shutterstock
Pic 2- Solutions Review
Pic 3 – TechTarget
Pic 4 – StrongDM